Who is My Mobile Use | Savergram
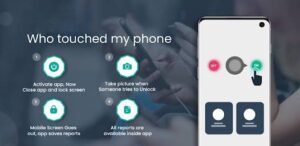
Who My Mobile use is a security application designed to monitor Savergram unauthorized access to your smartphone.It uses the front camera to capture photos of anyone who unlocks your device without permission. The app features two modes:
one for silently recording usage and another that triggers an alarm if the phone is accessed. Available on both Android and iOS, WTMP offers various subscription options for premium features, enhancing its functionality and security capabilities. 📸📱

The is a security application designed to enhance the protection of mobile devices against theft. Its notable features include:
1. Intruder Selfies: This feature captures photographs of individuals who attempt to unlock the phone without authorization.
2. App Usage Logging: The application maintains a record of the applications accessed following an unauthorized unlocking attempt.
3. Alarm System: In the event of tampering, the phone activates a loud alarm, even when in silent mode.
4. Charge Alert: Users receive notifications if the charging cable is disconnected.
The application operates discreetly in the background, ensuring continuous monitoring of the device’s security.
employs several distinct mechanisms to differentiate between authorized and unauthorized users:
1. Silent Photo Capture: discreetly captures photographs of individuals who make multiple unsuccessful unlock attempts or handle a locked device without authorization. These “intruder selfies” are securely stored within the app’s reports section.

2. Tamper Alarm: can be configured to activate a loud alarm if the device is tampered with, even when in silent mode. This alarm can only be deactivated by inputting the correct PIN, ensuring that only authorized users can disable it.
3. Motion Detection Alarm: The app features a “Do Not Touch My Phone” (DTMP) function that utilizes the device’s built-in sensors to detect motion. Any attempt to move or disturb the device triggers an alarm that can only be stopped by entering the PIN.
It is important to note that does not access or store any personal data from the user’s device. All captured photographs and logs are securely retained within the app itself.
In summary, leverages silent photo capture, motion detection alarms, and secure data storage to effectively distinguish between the device owner and unauthorized individuals attempting to access the device.
Who Touched My Mobile incorporates several robust measures to safeguard personal data from unauthorized access:
Data Storage: All captured data, including photographs and logs, is securely stored locally on the user’s device, eliminating the risk of transmission to external servers and minimizing exposure to potential breaches.
Security Safeguards: implements stringent security measures to protect against loss, theft, and unauthorized access, ensuring the confidentiality and integrity of personal information.
User Control: Users retain full control over their data, including the ability to synchronize with Google Drive, empowering them to manage and safeguard their personal information autonomously.
Privacy Policy Compliance: The application strictly adheres to comprehensive privacy policies that clearly outline the collection and utilization of personal data, emphasizing lawful and ethical practices.
has recently introduced several new features to bolster mobile security:
Anti-Spyware Setup: This feature offers step-by-step checklists to ensure comprehensive protection against spyware on the user’s device. It facilitates the review and management of app permissions, thereby preventing unauthorized access to sensitive data.
Charge Alert: now activates an alarm when the charging cable is disconnected from the phone, promptly notifying users of potential unauthorized removal. The alarm can only be deactivated by entering a unique PIN.

Dynamic Theft Protection Mechanism (DTMP): By enabling DTMP, the app utilizes the phone’s built-in sensors to detect motion. If someone attempts to move or disturb the device, it triggers an alarm that requires the PIN to be entered to stop.
Anti-Theft Phone Protection: WTMP provides an anti-theft phone protection feature that employs the built-in sensors to trigger a motion alarm whenever someone tries to touch or disturb the device. Only the correct PIN can deactivate the alarm.
These new features, in conjunction with existing capabilities such as intruder selfies and the loud alarm system, provide users with enhanced security and control over their mobile devices.
The Anti Spy Setup feature in WTMP bolsters security by offering users a systematic checklist to safeguard against spyware. It empowers users to:
1. Review Application Permissions: Users can meticulously manage and limit application permissions, effectively preventing unauthorized access to sensitive data.
2. Verify Device Settings: The feature meticulously guides users in scrutinizing and fortifying their device’s inherent protection settings, ensuring they are consistently updated and efficacious.

3. Comprehensive Protection: By meticulously educating users on potential vulnerabilities, it facilitates the establishment of a robust defense against spyware and other malevolent threats, thereby enhancing the overall security of the device.
The Anti Spy Setup feature in WTMP contributes to enhanced security against spyware by providing users with checklists to review app permissions and device settings. These checklists assist users in taking proactive measures to safeguard their devices against potential spyware threats.
However, it is important to note that the Anti Spy Setup feature does not possess real-time spyware detection and blocking capabilities like a dedicated antivirus application. Its primary focus lies in educating users about best practices to prevent spyware infections.
For active detection and removal of spyware, users may consider employing a specialized anti-spyware application such as ProtectStar Anti Spy. This application utilizes AI-powered scanning to identify and eliminate spyware threats in real-time.
In summary, while the Anti Spy Setup feature offers valuable security measures to strengthen device protection against spyware, it is not a comprehensive substitute for a robust anti-spyware solution. For thorough real-time protection, users may need to supplement the WTMP app’s security features with a separate anti-spyware application.
To utilize the Who Touched My Phone application, adhere to the following guidelines:
1. Acquisition and Installation:
– Obtain the application from the designated Google Play Store or Apple App Store.
2. Permission Authorization:
– Upon launching the application, grant the requisite permissions, encompassing device administrator privileges.
3. Activation Procedure:
– Subsequent to the configuration process, select the activation button. Subsequently, close the application and secure your device by locking it.
4. Monitoring Function:- The application will automatically document any unauthorized attempts to unlock your device, capturing photographic evidence of potential intruders.
5. Report Accessibility:
– Within the application, access the reports to ascertain individuals who attempted to unlock your device and the actions they undertook.
6. Alert Configuration:
Wait for few seconds
[su_button id=”download” url=”https://play.google.com/store/apps/details?id=com.wtmp.svdsoftware” size=”6″ icon=”icon: arrow-circle-down” text_shadow=”0px 0px 0px #000000″]Click to Download App ✅️[/su_button]
– Configure alarm settings to bolster security measures against unauthorized access.
This streamlined setup facilitates efficient monitoring and protection of your device.
Disclaimer
Modes of Operation: The app’s got your back, recording unauthorized access with its front camera 📸 and sounding the alarm if someone tries to unlock your device without permission! 🚨
Subscription Model: Level up your experience with premium subscriptions for enhanced features! 🔝 Auto-renewal options available for your convenience.
Privacy Practices: We value your privacy! 🔒 The app may collect identifiers and usage data, but rest assured, it’s all anonymous. Your identity stays safe with us.